A new study on the topic of Cybersecurity and the proliferation of cyberattacks against Small and Medium-Sized Businesses (SMB) was released this last year. Historically, criminals would focus attacks on larger enterprise level organizations in an effort to reap a much larger reward. However, the level of technical expertise needed to infiltrate these companies’ security required significant time and investment in order to successfully, if ever, penetrate the network. Soon, attacks were redirected toward a much easier target, SMBs, who often lack the budget or in-house expertise to prevent the same potential attacks, resulting in a higher frequency in SMB breaches.
Rate of Attacks: In today’s environment, no business is too small to evade an attack or breach. For example, the study revealed of the more than 598 SMB respondents, nearly 55% said their companies experienced a cyber-attack, while 50 percent reported having a data breach involving customer and employee information, all within the past 12 months. What many SMBs don’t realize however, is that a breach often goes undetected for quite some time.
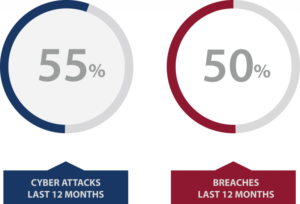
It is a staggering realization only compounded when you consider the average cost of the incidents being $879,582 in damages or the comparable theft of IT assets; this does not account for the disruption in operations which averaged $955,429, or the average company losing more than 5,000 individual records as a result of the breach.
Key Findings:
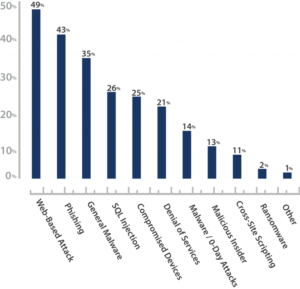
1. The most common attacks used against SMBs were Web-Based and Phishing/Social Engineering facilitated by negligent employees, contractors, and third parties sources.

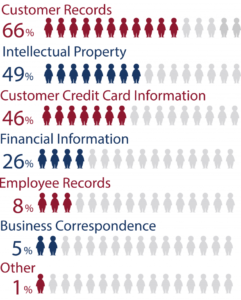
2. When companies where asked what information they were most concerned over losing from a cyberattack, the vast majority cited the potential loss or theft of customers’ information and intellectual property.
3. Strong passwords and biometrics were recognized by the respondents as an essential part of their security defense strategies. Yet, despite being acknowledged and incorporated as a part of their security practices, few organizations had visibility into their employees’ password practices, and/or rarely enforce their own written security policies.

4. To make matters worse, many current technologies are unsuccessful in detecting or blocking many of today’s targeted attacks. Most exploits have been engineered to evade detection systems or anti-virus solutions and rely on fooling end users to infiltrate otherwise secure networks and data.
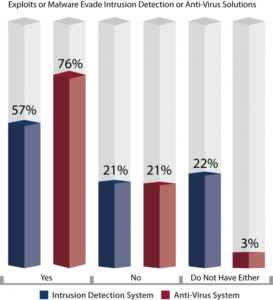
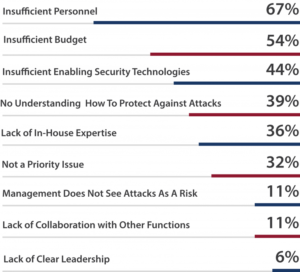
5. Some other factors contributing to the influx of intrusions are attributed to a lack of personnel, limited budgets, and insufficient or inappropriate technologies used to prevent these intrusions. The exhibit below outlines the prevalence of shortcomings throughout SMBs.
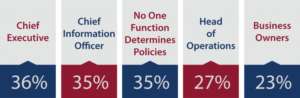
6. Determination of IT security priorities is not centralized. Some of the positions responsible are the Chief Executive and Chief Information Officer. However, thirty-five percent of respondents stated that no one position consistently determines the IT policies. This is a key role that requires expertise and knowledge of cyber security in order to make sound decisions that protects your business. Without clear guidance, the risks are often left unchecked.
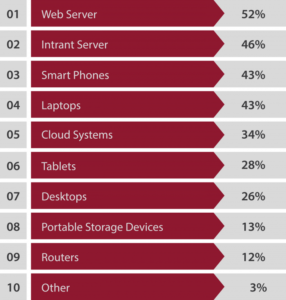
7. Web and intranet servers are the most vulnerable endpoints or entry points to network and enterprise systems, with fifty-two percent of respondents stating their companies’ Web Servers and forty-six percent of respondents saying their intranet servers are most vulnerable to attack. Yet despite this, many do not feel the threat of an attack is important enough to include in the current security strategy.
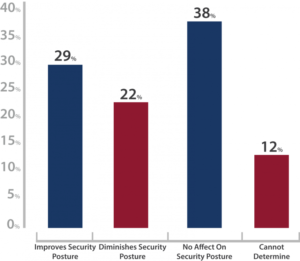
8. Despite the influx of cyber-attacks toward SMBs, unsecured cloud usage and mobile device access to business applications/infrastructure continue to become the industry standard, further weakening the network for future exploitation if the security of the information being transmitted is not also being taken into consideration. Nearly 29% believe the use of cloud services inherently improves their security posture, however, it is not enough to ensure protection against an attack, in fact, without proper network protection and end user education, you could open your entire cloud storage for anyone to grab.
Final Thoughts: While the continued advancement in technology has increased our mobility, access, and productivity, it has also made companies which were previously thought too small to be concerned with the potential risk of a cyberattack extremely susceptible to infiltration.
Many SMBs with budgetary constraints and limited expertise are now subject to the same security responsibilities of a company competing on the global scale. It is why having a trusted IT MSP is so vital to ensuring the safety and security of your company’s future.
