How To Recognize and Avoid Phishing Scams

Table of Contents
In today’s digitally-driven era, phishing scams present a significant cybersecurity threat. Essentially, a phishing scam is a deceptive tactic utilized by cybercriminals. They ingeniously pose as a trustworthy entity to trick individuals into divulging sensitive information like passwords or credit card details. The cornerstone of protection against these scams lies in understanding what they are, recognizing them, and knowing how to respond.
Understanding Phishing Scams
There’s a myriad of phishing scams, each characterized by its unique approach and execution:
Email Phishing: This is the most prevalent form of phishing scams. Cybercriminals send mass emails impersonating trusted organizations such as banks or service providers. These seemingly innocuous emails usually contain a sense of urgency and link to a counterfeit website designed to harvest your data once inputted.
Spear Phishing: Unlike email phishing, spear phishing is highly targeted. The fraudsters gather personal information about their target to make their fraudulent emails seem more convincing. This personalized approach increases the chances of the recipient falling for the scam.
Whaling: This method is a specialized form of spear phishing. Whaling targets high-profile individuals such as CEOs and CFOs. Due to the potential high return, attackers make substantial efforts to create highly tailored and convincing emails that mimic co-workers or known contacts.
Smishing and Vishing: These are phishing attacks conducted via SMS (Smishing) and Voice call (Vishing). In Smishing, the attacker sends a text message prompting the recipient to provide sensitive information or click on a malicious link. Conversely, vishing involves a phone call with the attacker posing as a bank official or service provider to trick the victim into revealing confidential information.
Recognizing Phishing Scams
Spotting phishing scams can be challenging, given the ever-evolving techniques scammers employ. You need to verify the sender’s information before acting on any instructions in the email. There are telltale signs to look out for, however, when recognizing a phishing scam.
- Look out for poor grammar and spelling errors. While not all phishing attempts will have them, many do.
- Be wary of emails or messages that evoke a sense of urgency, such as threats to close your account.
- Check the URL carefully. In many cases, the link URL won’t match the supposed sender’s address.
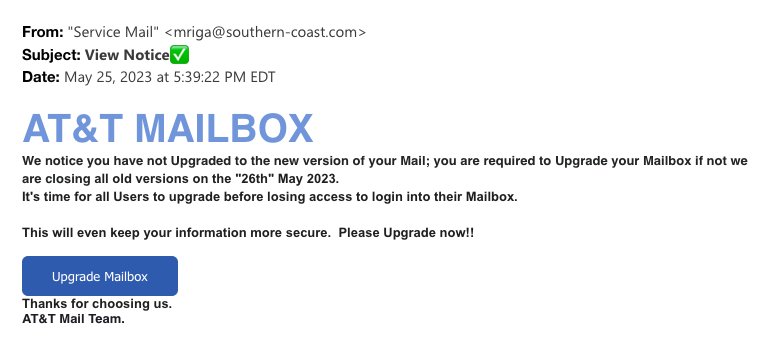
Here is an example of a real-life phishing scam. You’ll notice the “from” email is not congruent with AT&T branding.
How to Protect Yourself From Phishing
The Federal Trade Commission provides these comprehensive measures to guard against phishing attacks:
- Use Security Software: Ensure your computer has updated security software. Set the software to update automatically to protect your computer from new threats.
- Update Your Mobile Software: Similar to your computer, your mobile device is vulnerable too. Ensure the operating system and apps are updated regularly.
- Use Multi-Factor Authentication: This offers an additional layer of protection as it requires more than one verification form to access sensitive accounts.
- Data Backup: Regularly back up your data to safeguard against loss in case of a phishing attack.
Furthermore, practicing safe online behavior can go a long way in ensuring your cybersecurity. Please don’t click on suspicious links or share sensitive information online, and always make sure your software and security systems are updated. CyberGate IT can perform a vulnerability assessment test to determine how strong your network is against cyber attacks and where potential weaknesses are.
What To Do If You’ve Been Phished
If you suspect you’ve fallen victim to a phishing scam, it’s crucial to act swiftly:
- Change your passwords: Begin with the account you believe has been compromised, then change your other account passwords as a precaution.
- Report to the relevant authorities: Notify your bank or the online platform where the phishing occurred. They can take immediate steps to protect your account and may be able to assist law enforcement in catching the scammer.
- Update your software and security protection: Ensuring you have the latest software and security updates can prevent further exploitation of your information.
- It’s also of utmost importance to report the phishing scam. In the U.S., you can report phishing emails to reportphishing@apwg.org or the Anti-Phishing Working Group. You can also report the scam to the FTC.
Contact CyberGate IT For a Cyber Security Assessment
While the internet brings convenience, it also comes with threats such as phishing scams. Therefore, understanding these threats, recognizing them, and knowing how to respond is essential to your cybersecurity.
For a more comprehensive cybersecurity approach, consider engaging professional help. Here at CyberGate IT, our team of experts can perform a vulnerability assessment to identify weaknesses in your network and provide actionable solutions.
Staying vigilant and informed is your first line of defense in the digital world. Remember, it’s about protecting your computer and personal information and safeguarding your peace of mind. Contact us below to get started today.
FAQ About Phishing Scams and Small Businesses
The most common phishing scams include email phishing, spear phishing, and whaling. Other notable ones include Smishing and Vishing, which are phishing attacks conducted via SMS and voice calls, respectively.
Phishing scams trick individuals into revealing sensitive information, such as passwords, credit card numbers, or Social Security numbers, by pretending to be a reputable organization or individual.
A common example of a phishing scam is receiving an email that, at first glance, seems to be from your bank. The email might claim there’s an issue with your account and ask you to click on a link to enter your credentials. The link, however, leads to a fraudulent website, and the credentials entered are collected by the scammer.
Three common signs of phishing scams include: poorly written messages with spelling and grammar mistakes, an urgent or threatening tone aiming to rush you into action, and mismatched or suspicious URLs.
Phishing scams can target anyone, but they are often aimed at individuals who are less familiar with digital technology, such as older adults. High-level executives, known as ‘whales,’ are also targeted due to the potential high return.
Accordion The three most common online scams are phishing (fake emails, websites, or text messages), tech support scams (scammers pretend to be tech support to gain access to your computer), and online shopping scams (fraudulent websites offering too-good-to-be-true deals).
Yes, if you provide sensitive information such as your username, password, or credit card details in response to a phishing attempt, you are essentially giving hackers access to your accounts.
Phishers are typically after sensitive information that can be used for financial gain. This may include login credentials, credit card information, social security numbers, or other personal data that can be used for identity theft.
Replying to a phishing email or message can lead to your device being infected with malware, or your personal or financial information being stolen. If you suspect you’ve responded to a phishing attempt, it’s important to change your passwords and notify the appropriate authorities or companies immediately.
Phishing attempts often have certain signs, such as poor grammar or spelling, requests for personal information, generic greetings, and suspicious or mismatched URLs. Learning to recognize these signs can help you avoid falling for phishing scams.
Being aware of the tactics used by phishers and regularly updating your software and security measures can significantly reduce your risk of falling for a phishing scam. Always verify the source before clicking on links or providing personal information. If in doubt, contact the organization or individual directly using a known and trusted method.
