Cisco Security Report: 34% of Service Providers Lost Revenue from Attacks

“A new type of security threat — “destruction of service” (DeOS) attacks, which could eliminate companies’ backups and safety nets — could cause way more damage to businesses than ransomware. This is according to Cisco’s 2017 Midyear Cybersecurity Report in which the company coined the term DeOS attack. The report says the Internet of Things […]
Humans have become the primary attack surface for cyber criminals
“As the world goes digital, humans have moved ahead of machines as the top target for hackers. Ninety-one percent of attacks by cyber criminals start through email, according to email security provider Mimecast. These spear phishing attacks target humans, luring them to click on malicious URLs that place ransomware on their computers and phones. The […]
60% of small companies that suffer a cyber attack are out of business within six months

“It seemed like just another ordinary day for a small online retailer in the Midwest. Little did they know that the simple click of an e-mail link was about to threaten the entire business. One of the company’s employees received an e-mail with a link to a seemingly benign catalog. One click and the company’s […]
43 Percent of Cyber Attacks Target Small Business
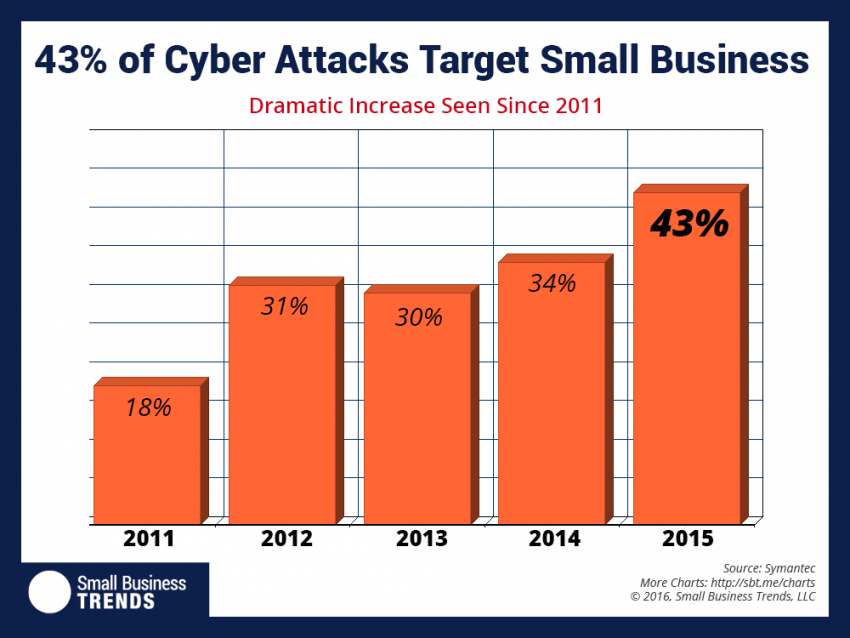
“Cyber crime is on the rise and small businesses are increasingly becoming the target of hackers. New data from Symantec’s 2016 Internet Security Threat Report shows that small businesses have become a big target for phishers. Last year, phishing campaigns targeted small businesses (PDF) 43 percent of the time. That’s up 9 percent over 2014 […]
Cybercrime Costs to Reach $8 Trillion by 2022

“Some 2.8 billion data records expected to be breached in 2017, according to a report released today by Juniper Research. Cybercrime costs are expected to saddle businesses with a whopping $8 trillion price tag over the next five years, as connectivity to the Internet rises but security system upgrades don’t keep pace, according to a […]
MEDICAL DEVICE MAKERS EXPECT ATTACKS WITHIN NEXT YEAR, BUT AREN’T PREPARED

“A new survey found 67 percent of medical device manufacturers and 56 percent of healthcare delivery organizations (HDOs) believe their devices are likely to be the target of a cyberattack within the next 12 months. While many companies are concerned about the possibility of an imminent attack, most manufacturers remain unprepared. Just 17 percent of […]
Data Breach, Vulnerability Data on Track to Set New Records in 2017

“There are so far 1,254 publicly reported data breaches and 4,837 published vulnerabilities in the first quarter of this year. Enterprise security executives looking for metrics to justify their budgets to top management should have plenty of material to choose from for the rest of year. Two reports from Risk Based Security this week show […]
STUDY REVEALS MORE THAN 50% OF SMBS HAVE EXPERIENCED A DATA BREACH IN PAST YEAR

A new study on the topic of Cybersecurity and the proliferation of cyberattacks against Small and Medium-Sized Businesses (SMB) was released this last year. Historically, criminals would focus attacks on larger enterprise level organizations in an effort to reap a much larger reward. However, the level of technical expertise needed to infiltrate these companies’ security […]
Cybersecurity spending outlook: $1 trillion from 2017 to 2021

“Worldwide spending on cybersecurity is predicted to top $1 trillion for the five-year period from 2017 to 2021, according to the Cybersecurity Market Report, published by Cybersecurity Ventures. “IT analyst forecasts are unable to keep pace with the dramatic rise in cybercrime, the ransomware epidemic, the refocusing of malware from PCs and laptops to smartphones […]
‘Cyber Crime Is The Greatest Threat To Every Company In The World’

“The British insurance company Lloyd’s estimates that cyber attacks cost businesses as much as $400 billion a year, which includes direct damage plus post-attack disruption to the normal course of business. Some vendor and media forecasts put the cybercrime figure as high as $500 billion and more. Then there’s the hacks and breaches which go […]
